Consul
Consul is a service mesh solution that provides a dedicated infrastructure layer to basically solve the challenges of microservices architecture, some of its main key features are:
-
Enables dynamic discovery of new instances.
-
Share, synchronize and store key-value between instances.
-
Provide an ACL system and enable traffic encryption.
-
Provide a healthcheck service that return the health state of differents services.
-
Provides a cluster of server nodes to ensure high availability.
This plugins offers the possibility to fetch key-value either from Consul server nodes or Consul agent nodes and then use them as Rudder Variables according to your needs. The Rudder server does not need to access the Consul server to get key-value, only the Rudder agent will do so.
Installation
-
You’re supposed to already have your Consul environment configured, with differents keys-values that can be: Indexed objects, configuration parameters or metadata.
-
Install the plugin on your Rudder server
-
Once the plugin is installed, you need to edit the configuration file in
/var/rudder/plugin-resources/consul.jsonon each agent. This config file must contain the address of your Consul server and the optional token parameter in case your Consul server is configured with one. A sample config is inshare/plugins/consul/sample_consul.json.
Usage
Use the Variable from Consul generic method in Rudder to fetch key-value and make sure that the agent has a proper consul.json configuration.
Example of usage :
-
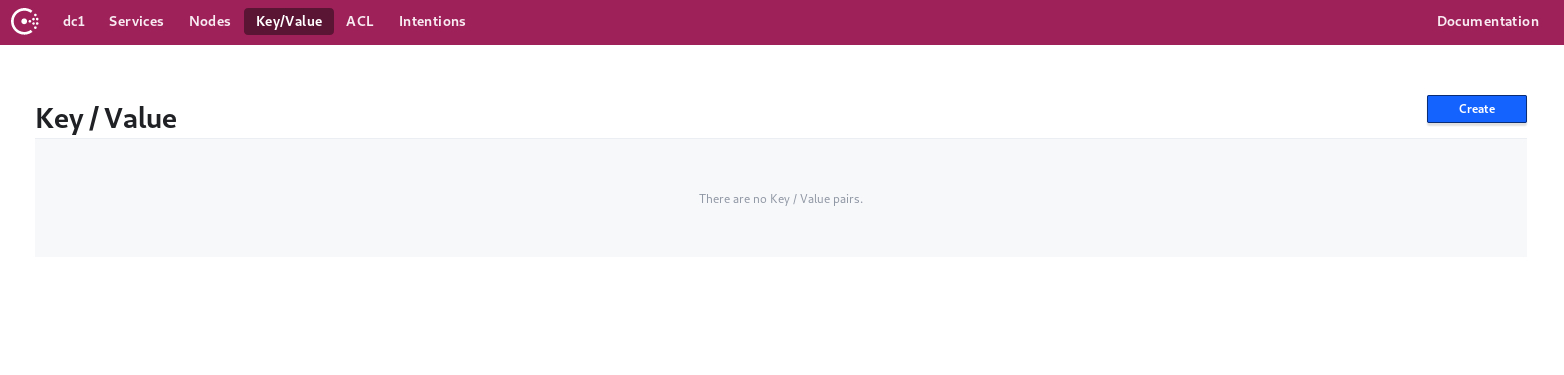
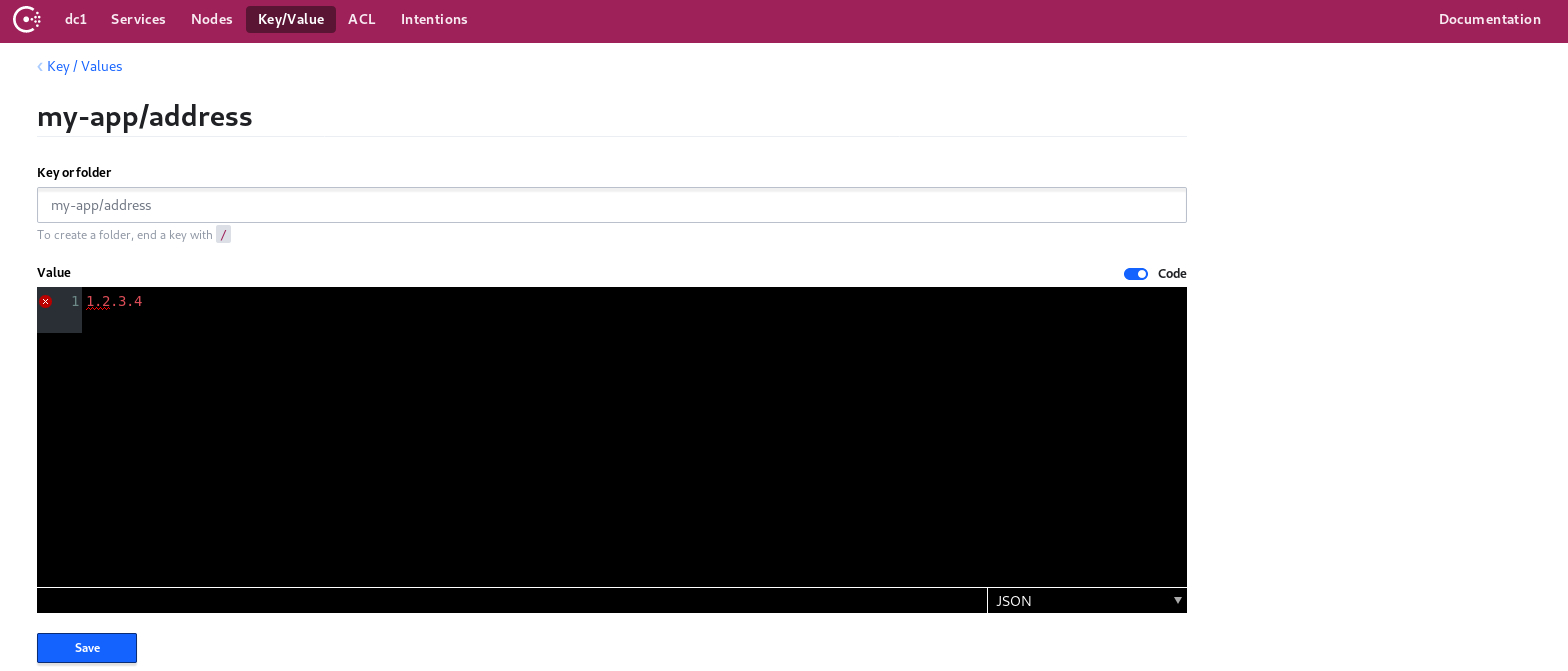
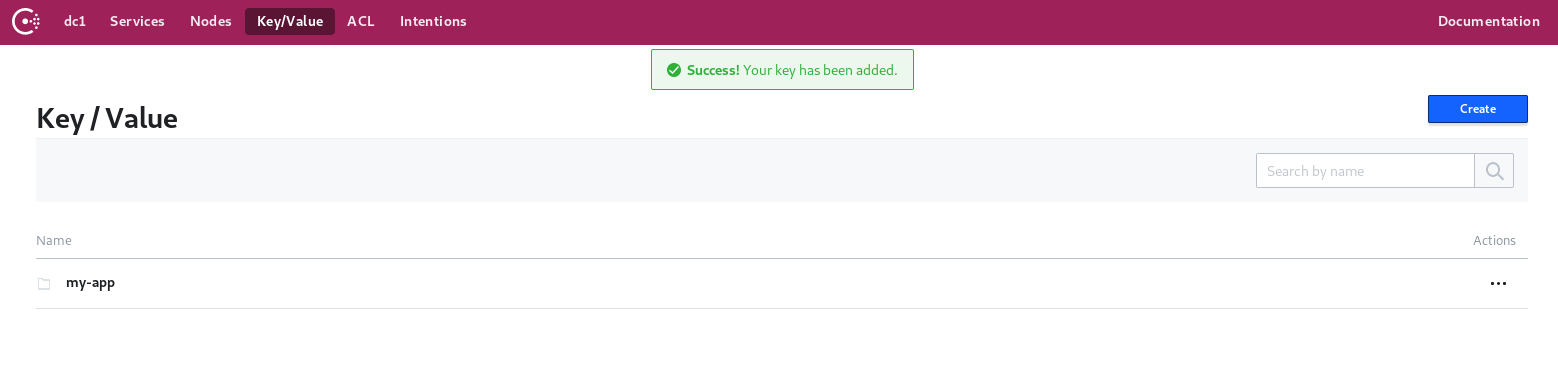
Key-value storage via Consul Web Interface:
One of the main key features of Consul is that it provides reliable and hierarchical key-value storage where keys are separated by (/).
Start by configuring a key-value pair that contains two hierarchical levels: my-app and address.
-
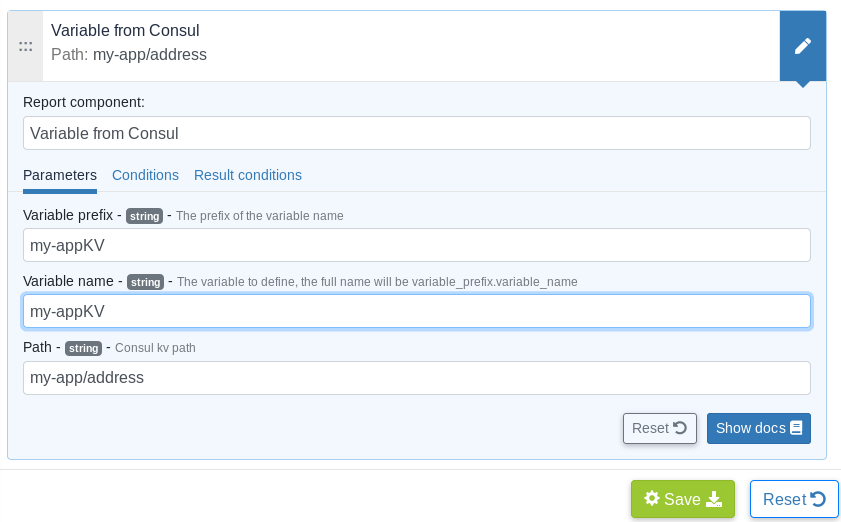
Fetch key-value via Rudder Server technique editor:
Now that you have finished setting up the key-value in Consul, you need to define the generic method on the Rudder technique editor by configuring a variable prefix, variable name and most importantly the path to the key-value.
← CIS CVE →